A data breach may lead to various dangers coming upon an individual and/or organization in serious financial, reputational, legal, and operational results. There is considerable potential for financial loss due to fines, compensation to affected individuals, and investigations. Business disruption or shutdowns during the time the breach is being addressed may affect the organization's business. Losing customer and client trust and canceled contracts will eliminate future revenue.
Fujitsu is a global technology giant and it experienced a malware-based attack that affected multiple workstations. The breach raised concerns over the exposure of sensitive information, although specific data compromised was not disclosed. In Bank of America, over 57,000 customers had their personal data exposed due to a ransomware attack targeting one of the bank's service providers. Information such as social security numbers, birthdates, and account details were among the compromised data. Vans is also a well-known shoe brand that suffered a breach where customer information was potentially exposed. Although detailed financial information was reportedly not affected, there were concerns over identity theft risks for affected users.
Why breach of data must be prevented?
1. Financial Loss Prevention
Data breaches often lead to significant financial losses due to fines, lawsuits, remediation costs, and lost business opportunities. The global average cost of a data breach is now over $4 million, according to IBM’s 2023 Cost of a Data Breach report.
2. Protecting Customer Trust
Trust is critical for businesses. If a company loses customer data, it risks damaging its reputation and losing customer loyalty. Rebuilding this trust can take years and may result in a permanent loss of customers.
3. Preventing Identity Theft
Breached data often includes sensitive information like Social Security numbers, credit card details, and personal identities. Preventing breaches helps protect customers and employees from identity theft and the long-term consequences of financial fraud.
4. Maintaining Competitive Advantage
For businesses, intellectual property (IP) and proprietary information are crucial assets. A breach could result in IP theft, giving competitors an advantage or causing a loss in market share.
5. Legal and Regulatory Compliance
Organizations are subject to strict data protection laws like the GDPR, CCPA, and HIPAA. Failing to prevent breaches can result in heavy fines and legal repercussions, along with operational restrictions.
6. Business Continuity
Breaches can disrupt operations, forcing businesses to shut down systems for investigation and recovery. The downtime can lead to lost revenue, missed opportunities, and a damaged brand image.
7. Cybercrime Deterrence
Data breaches encourage further cybercrime, as leaked information can be sold on the dark web. Preventing breaches helps reduce the profitability and incentive for hackers to target organizations.
8. Cost of Remediation
The cost of cleaning up after a breach—such as forensic investigations, patching security flaws, notifying affected individuals, and managing public relations—is far higher than implementing preventative security measures.
9. Preserving Brand Reputation
A company’s reputation can be permanently damaged by a breach, particularly if it mishandles the response. Reputation loss can lead to decreased sales, a drop in stock prices, and long-term harm to the brand’s image.
10. Avoiding Intellectual and Data Manipulation
Beyond data theft, breaches can result in data manipulation, which may go undetected for extended periods. Manipulated data can lead to incorrect business decisions, flawed research, and financial losses.
11. Business continuity
This means that by avoiding breaches, organizations also avoid the kind of disruptions that could cripple their operations, like system shutdowns, data recovery, or investigations. In addition, it saves them from the headache of having to juggle business growth, innovation, and strategic priorities in the face of cyber incidents or crisis management.
- Reduced risk of cybercrime: An effective data breach prevention strategy will minimize the organization's appeal as a target to hackers, reducing its likelihood of being targeted through various cyberattacks involving ransomware or phishing. Companies with good cybersecurity practices minimize risks of breaches trickling down into their supply chain and thus contribute to better protection for partners and vendors.
- Protection of customer data: Data breach prevention prevents customer data from being compromised. This way, organizations can protect their policies of privacy and ethical commitment to their clients. Protection of customer data can lead to better and long-lasting relationships built on trust and security.
12. Savings on IT and Security Management
Breaches that are avoided do not require costly remediation, incident response work, and overall system overhauling. Instead of responding to breaches, an organization may well apply its resources in more fitting ways to enhance the overall IT infrastructure and security posture.
Comparison Table
| Prevention measures | Working Principle | Advantages | Shortcomings |
| Implement Strong Access Controls |
|
|
|
| Encrypt Sensitive Data |
|
|
|
| Regular Patch Management | Automated and scheduled patch updates |
|
|
| Employee Training & Awareness |
|
|
|
| Regular Security Audits & Penetration Testing |
|
|
|
| Network Segmentation |
|
|
|
| Adopt a Zero Trust Architecture |
|
|
|
| Backup Data Regularly |
|
|
|
| Monitor and Respond in Real Time |
|
|
|
| Secure Endpoint Devices |
|
|
|
10 Proactive Measures to Reduce the Risk of Breaches
1. Implement Strict Access Controls
Multi-Factor Authentication (MFA): Ensure that MFA is enforced for all critical systems and applications. This adds an extra layer of security by requiring users to provide two or more forms of identification before accessing sensitive data.
Principle of Least Privilege: Adhere to the principle of least privilege, where users are granted only the minimum levels of access necessary to perform their job functions. Regularly review and update access rights to ensure they remain appropriate.
2. Encrypt Sensitive Data
Data at Rest and in Transit: Implement robust encryption for sensitive data both at rest (stored data) and in transit (data being transferred over networks). This ensures that even if data is intercepted or accessed without authorization, it remains unusable.
Strong Encryption Algorithms: Utilize strong encryption algorithms such as AES-256, which are widely recognized for their security. Additionally, implement a comprehensive key management system to securely manage encryption keys.
3. Periodic Patch Management
Timely Patching: Regularly apply the latest security patches for all software, operating systems, and devices. This helps to mitigate vulnerabilities that could be exploited by attackers.
Automated Patching: Automate the patching process wherever possible to reduce human error and ensure timely updates. This can be achieved through patch management tools that automatically identify and apply necessary patches.
4. Employee Training & Awareness
Regular Training: Conduct regular cybersecurity training sessions to educate employees about common threats such as phishing, social engineering, and unsafe internet practices.
Security Culture: Foster a security-conscious culture within the organization. Encourage employees to report suspicious activities and provide clear guidelines on how to do so.
5. Conduct Regular Security Audits and Penetration Testing
Vulnerability Scanning: Perform regular vulnerability scanning to identify and address potential weaknesses in the system. This includes both automated scanning tools and manual penetration testing.
Log Inspection: Periodically inspect system logs for any suspicious activity. Implement log management solutions to centralize and analyze logs from various sources.
6. Network Segmentation
Isolating Sensitive Data: Segment sensitive systems and data from the general corporate network. This limits the potential impact of a breach by isolating critical assets.
Traffic Monitoring: Configure firewalls, Intrusion Detection Systems (IDS), and Intrusion Prevention Systems (IPS) to monitor traffic between different network segments. This helps in detecting and preventing unauthorized access.
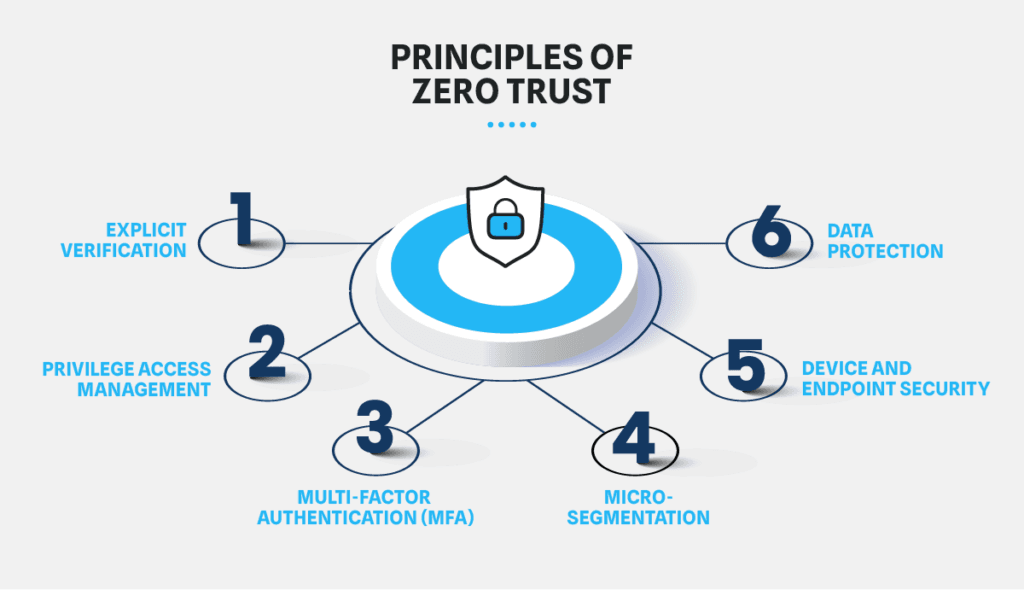
7. Zero Trust Architecture
Assume Breach: Adopt a Zero Trust Architecture, which assumes that threats can exist both inside and outside the network. Every access request is treated as a potential threat, regardless of its origin.
Continuous Monitoring: Implement continuous monitoring and authentication for all access requests. Use advanced analytics to identify and respond to anomalies in real-time.
8. Data Backup Regularly
Regular Backups: Regularly back up sensitive data to a segregated, secure location. Ensure that backups are encrypted and stored offsite to protect against physical threats.
Backup Testing: Periodically test the restoration of backed-up data to ensure its integrity and dependability. This is crucial for quick recovery during data breach incidents.
9. Real-time Incident Monitoring and Response
SIEM Systems: Utilize Security Information and Event Management (SIEM) systems to collect and analyze security information in real-time. This helps in detecting and responding to security incidents promptly.
Incident Response Plan (IRP): Develop and maintain an Incident Response Plan (IRP) that outlines the steps for detecting, containing, and responding to security breaches. Regularly test and update the IRP to ensure its effectiveness.
10. Secure Endpoint Devices
Endpoint Protection: Deploy comprehensive endpoint protection solutions that provide multi-layer defense against threats. This includes antivirus software, firewalls, and Mobile Device Management (MDM) solutions.
Secure Remote Access: Provide secure remote access to corporate data, especially for remote workers. Implement Virtual Private Networks (VPNs) and other secure access methods to protect data in transit.
FAQs
Q: How do proactive measures differ from reactive measures?
A: Proactive measures are those taken before an incident occurs and, as such, avoid such incidents. An example of this could be setting up a firewall, encrypting data, among other security actions that can fall under proactive measures. Reactive measures insinuate incident response after they happen; reconstituting data from backups or looking at what actually happened if there has been a breach.
Q: Can small businesses use proactive measures?
A: The answer is yes, small businesses are also vulnerable to this sort of attack, and proactive measures may help them a lot. Strong access control, training employees, and regular backups could be pretty inexpensive with substantial protection against common threats.
Q: In what sequence should we prioritize the proactive measures to put into place?
A: It goes without saying that the basis would be the risk profile of the organization in question, the resources available, and the sensitivity of the data handled. Generally speaking, a sound foundational defense would include multi-factor authentication, patching on a regular schedule, and employee training.
Q: What are the typical complications in implementing these proactive measures?
A: Some of them are:
- Implementation Cost: Most proactive security measures, like MFA, encryption, and advanced monitoring systems, are relatively costly to deploy. This is mostly a problem for small and medium-scale businesses. Most firms suffer when it comes to finding a balancing point between the budget for security against the other needs of the business.
- Most proactive security tools are integrated with the existing system; this can prove very complex and take longer to implement. For example, the latest security technologies such as Zero Trust Architecture may not be easily supported by some of the older legacy systems.
- User Resistance: Employees push back against security controls creating speed bumps in their workflow, such as MFA, password policies, and constant security updates. The resistance almost always leads to poor compliance with the policy or unsafe workarounds.
Q: How is proactive breach prevention success measured?
A: Success in proactive breach prevention can be addressed by various metrics and indicators reflecting the strength of security controls. You can know how many unauthorized access attempts, phishing attacks, and malware firewalls and intrusion detection systems block among other preventive measures. High block rates are a sign that successful defenses stop the breach before it ever occurs. You will also have to take the time it takes to detect the security threat or suspicious activity that occurred.